Using Takeout Data Protection Tool
The Data Protection Tool manages the encryption keys for the Aloha Takeout product, to protect stored credit card information in accordance with the PCI-DSS specification. The Takeout Data Protection Tool allows the key custodian to establish or change the site key for the Aloha Takeout site. The key custodian should run the Takeout Data Protection tool.
Purpose of a site key
The Aloha Takeout application requires the presence of a site key to collect and store sensitive cardholder information. The site key encrypts the sensitive data before it is stored in the database or transmitted between client terminals and the server. When a customer wants to pay for a transaction with a stored payment card, Aloha Takeout retrieves and unencrypts this information in the background, and passes it to the Aloha POS for use with Aloha EDC in the normal payment process. The system also requires the site key for online orders with credit card payments, even though the site may not be storing credit card information with their customers. Until you establish a site key in the system, you cannot enter cardholder information using the ATO application.
Some best practices for site key management are as follows:
- Use a unique site key at each location.
- Restrict access to site keys to the smallest number of employees possible.
- Store site keys in a secure manner.
- Document and implement key management procedures.
- Require key custodians to sign a form affirming they understand and accept their key-custodian responsibilities.
- Generate strong keys, using uppercase and lowercase letters, numbers, and symbols.
- Change the site key at least quarterly, documenting each change of the key.
- Destroy all copies of the old key.
- Establish split knowledge and dual control of keys. For example, give sequential parts of the key to three different people, so that they all have to enter their own part, in a specific order, to reconstruct the whole key. Three parts of an example key could be 'MarYhad&,' 'AliTTle42@,' and 'laMb95&3.' The entire key would consist of these three parts, typed sequentially: MarYhad&AliTTle42@laMb95&3
- Prevent unauthorized substitution of the key.
- Replace keys known or suspected to have been compromised.
How the system stores and rotates a site key
The system stores site key information in the ATO\Data directory in an encrypted file called ATO_SK.dat. When you change the site key, the system changes the name of the existing ATO_SK.dat to ATO_SK1.dat and stores the new site key in ATO_SK.dat. When ATO needs to decrypt credit card information, it attempts to use ATO_SK.dat. If this fails, it tries ATO_SK1.dat, ATO_SK2.dat, etc. until it either decrypts or runs out of site key archives.
In most cases the ATO\Data directory should only contain one ATO_SK.dat file. When you restart the Radiant Takeout and Delivery service, it goes through the stored credit cards in the SQL database and re-encrypts them with the new key. When complete, the system deletes ATO_SK1.dat, and any other archives.
Anytime you establish or modify a site key, you must restart the Radiant Takeout and Delivery service and restart each instance of ATO running on a FOH terminal, to allow the new site key to take effect.
Establishing your initial site key
When running the Takeout Data Protection Tool for the first time, the main window appears with the Create Key button available for use.
- Navigate to Aloha Takeout\Bin directory.
- Double-click TakeoutDataProtectionTool.exe.
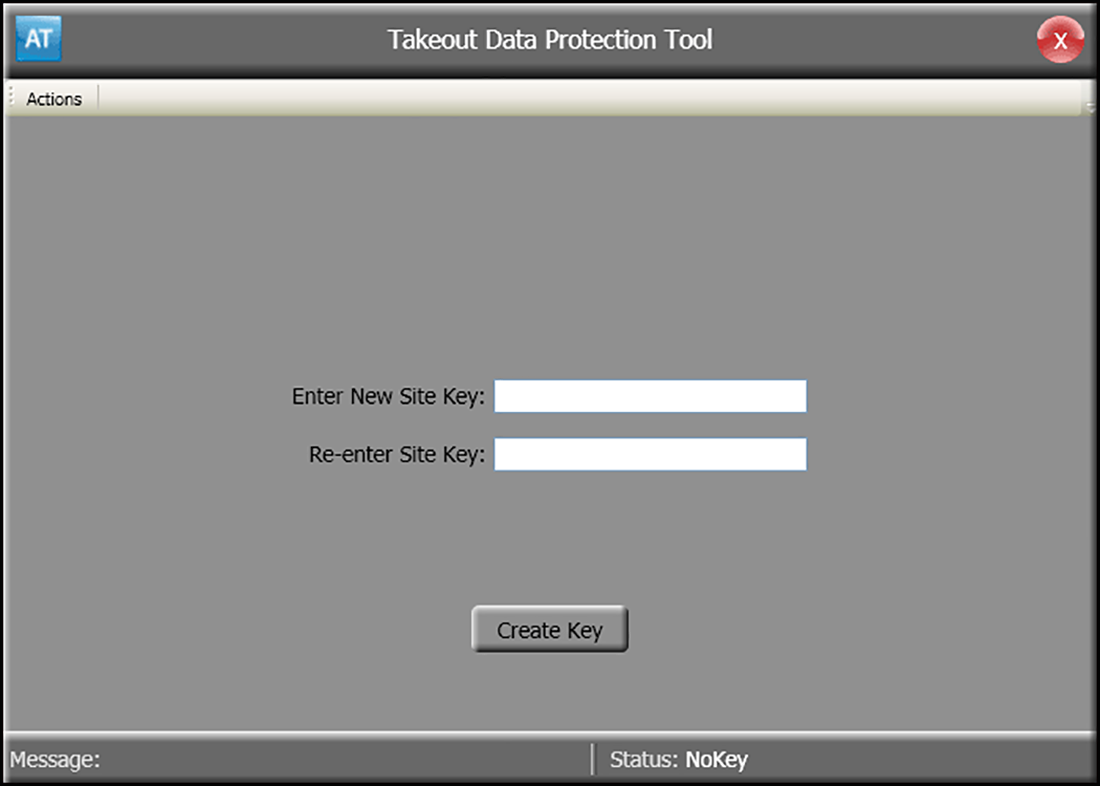
- Enter and re-enter the new site key.
- After initially entering the site key, the system requires you to enter the site key to perform any further actions.
Once established, the site key remains in effect until changed. Aloha Takeout provides full message support for any errors in key number entry that may occur.
Note:** The site key resides in the encrypted file \Aloha Takeout\Data\ATO_SK.dat. If the site key is forgotten or becomes corrupt, you can delete this file and enter a new site key. If this becomes necessary, all stored payment card information becomes unavailable for future use. Contact your NCR team member for help, before you delete this file.
Changing an existing site key
To rotate the key at a site, you must enter the site key to unlock or select Change Site Key from the Actions menu.
The form for changing the site key is similar to the form for setting the initial site key. In addition to the two fields for entering the new site key, you first receive a prompt to supply the existing site key. When you click Change Key, the tool validates the supplied existing key matches the value stored within the ATO system. The application also validates that both of the new key strings are identical. If the validation criteria are satisfied, the system saves the new key to the system. If any criteria fails validation, you receive a prompt to re-enter the keys.
- Navigate to the AlohaTakeout\Bin directory.
- Double-click TakeoutDataProtectionTool.exe.
- Type the current key in 'Enter Site Key.'
- Click Actions.
- Click Change Site Key.
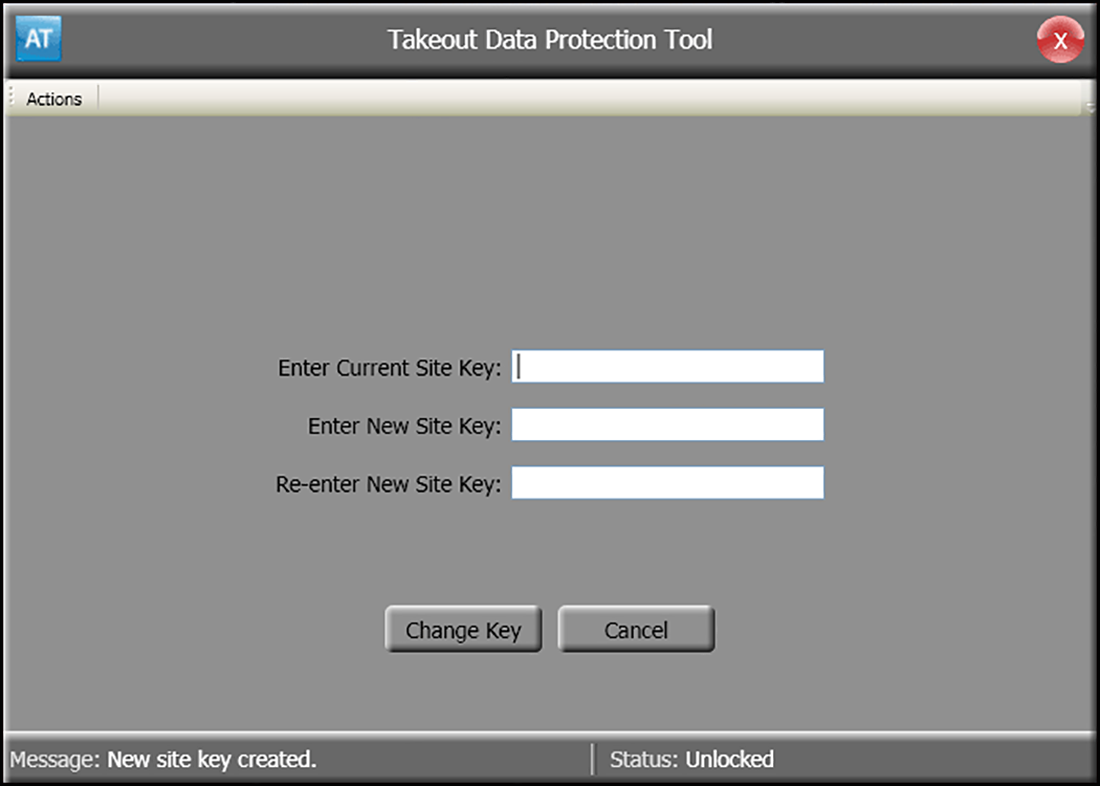
- Type the existing site key in 'Enter Current Site Key.'
- Type the new site key in 'Enter New Site Key.'
- Re-type the new site key in 'Re-enter New Site Key.'
- Click Change Key to confirm the change.
- Re-type the new site key in 'Re-enter New Site Key.'
Clearing credit card data
The Takeout Data Protection Tool also allows you to clear stored credit card information at a site.
- Navigate to the AlohaTakeout\Bin directory.
- Double-click TakeoutDataProtectionTool.exe.
- Type the current key in 'Enter Site Key.'
- Click Unlock.
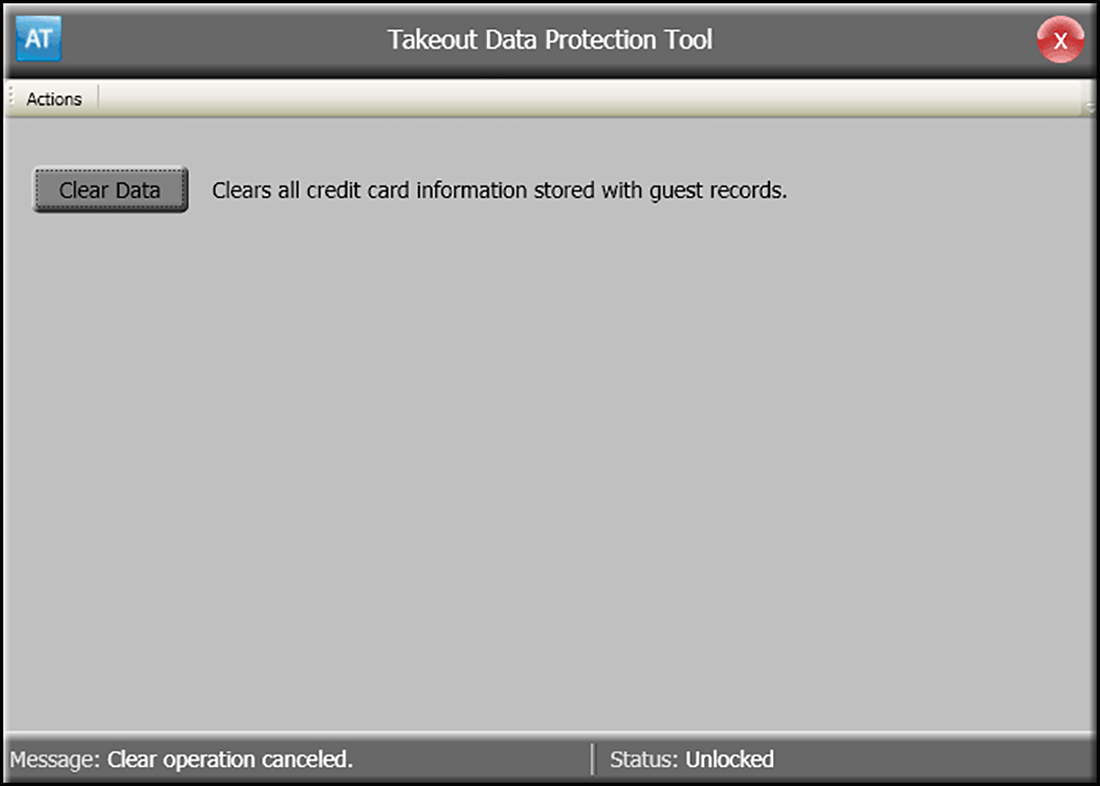
- Click Clear Data.
- Click Yes to confirm clearing all credit card information from the ATO database.