Aloha Spy
Core Product: Aloha Quick Service and Aloha Table Service
Complimentary Products: No
Separate License Required? No
Other References: Aloha Quick Service Manager Guide; Aloha Quick Service Server Guide; Aloha Quick Service Reference Guide; Aloha Table Service Manager Guide; Aloha Table Service Server Guide; Aloha Table Service Reference Guide
View/Download/Print: Aloha Spy Feature Focus Guide - HKS1672
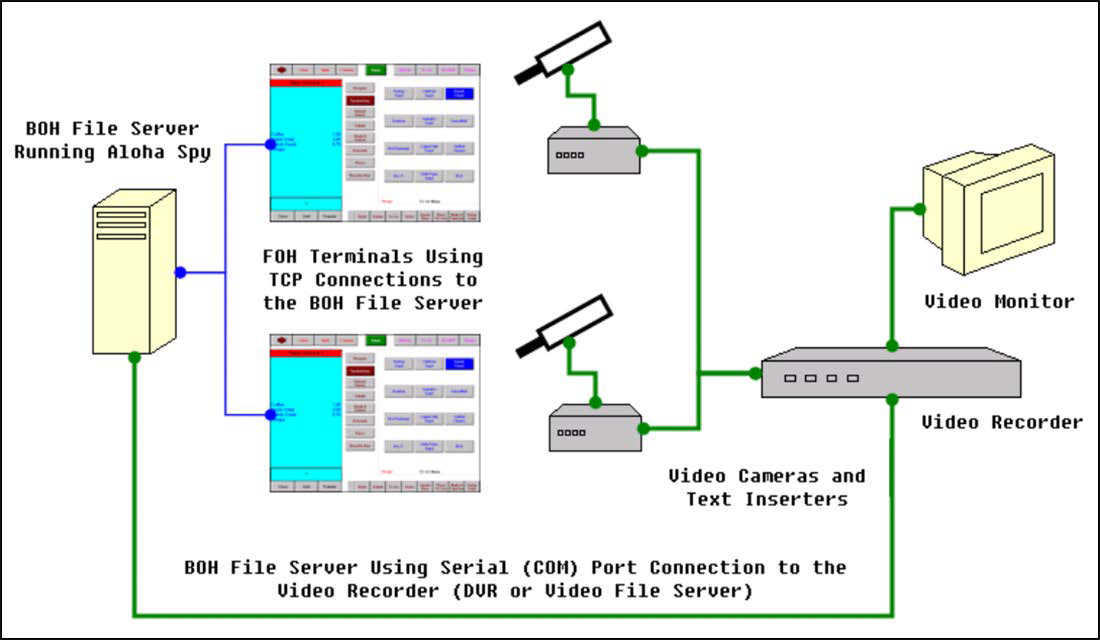
The Aloha® Point-of-Sale (POS) system uses the Aloha Spy feature to interface with video security systems. AlohaSpy.exe, part of the Aloha POS system, gathers information from Front-of-House (FOH) terminals via TCP network connection through a specific, user-specified TCP port. AlohaSpy.exe passes this information through an appropriate serial port (COM port) to the security system at a user-specified IP address. Some security systems may alternatively make use of USB or RJ45 connections, but these connection types are proprietary, and may use their own program files in conjunction with AlohaSpy.exe.
Video cameras transmit their images to the security system using the Aloha network or a direct connection to the security system, to one or more remote video monitors. The monitors display images from the cameras with text superimposed over them, as provided and formatted by the security system based on information received from AlohaSpy.exe. The text appearing over the video image reflects actions taken by employees as they use the FOH terminals.
The amount of data, and the method by which it displays on the video monitors may be configurable, based on the system supplied by the manufacturer. Each manufacturer defines the way in which it superimposes text over video images received from the cameras. Text may appear in columns, tables, separate windows, or any combination of these. Textual information appearing on the monitor reflects real-time activities taking place on the terminal, and also becomes part of the image, as recorded in the storage depot. Security systems may store the video signal on a DVR, or they may use a secondary file server.
The Aloha system also records information about transactions and operator actions to a Debout.spy file, as operators touch FOH functions.
Tip:
Hardware configuration for Aloha Spy is entirely dependent upon the security system in use. Figure 1 shows only one example of hardware configuration a security system manufacturer may require.
You can install any application required by the installed security system on the FOH terminals without having to register CtlSvr on the terminals. Aloha Spy detects CtlSvr running on the Aloha BOH file server, across the Aloha network, and functions accordingly.
Please contact your NCR Voyix Account Executive or Authorized NCR Voyix Partner for the most up to date information regarding security systems recommended for use with the Aloha POS system and Enterprise Solutions.
Configuring Aloha Spy
- Locating available ports
- Enabling and defining Aloha Spy functionality
- Configuring terminals to use Aloha Spy
- Creating the AlohaSpyPort environment variable
- Refreshing the POS data
Creating and configuring Alohaspy.ini and Debout.spy
Learn how to create and configure Alohaspy.ini and Debout.spy.